
| Home | Info | About Us | FAQ | Contact Us |
How The Soviets Are Bugging AmericaWhen the Reagan administration sent 55 Russian 'techicians' packing last fall, it put only a slight dent in Russia's U.S. spy network
|

|
|||||
|
||||||
Soviet agents may be listening to your personal telephone conversations. If you're involved in the government, in the defense industry or in sensitive scientific activity, there is a good chance they are.
In fact, a recent unclassified Senate Intelligence Committee report on counterintelligence indicates more than half of all telephone calls in the United States made over any distance are vulnerable to interception. Every American has a right to know this.
You should also know that the Reagan administration has recognized this threat for a long time now, but so far, the bureaucratic response has been piecemeal, and at times reluctant.

Consider this as background: In 1975, when I was named permanent U.S. representative to the United Nations, Vice President Nelson Rockefeller summoned me to his office in the Old Executive Office Building. There was something urgent he had to tell me. The first thing I must know about the United Nations, he said, is that the Soviets would be listening to every telephone call I made from our mission and from the ambassador's suite in the Waldorf Towers. I thought this a very deep secret, and treated it as such. Only later did I learn that Rockefeller had publicly reported this intelligence breach to the president in June 1975. The Rockefeller Report to the President on CIA Activities Within the United Nations notes:
"We believe these countries (communist bloc) can monitor and record thousands of private telephone conversations. Americans have a right to be uneasy if not seriously disturbed at the real possibility that their personal and business activities, which they discuss freely over the telephone, could be recorded and analyzed by agents of foreign powers."
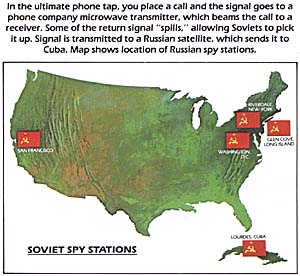
The Soviets conduct this eavesdropping from their "diplomatic" facilities in New York City; Glen Cove, Long Island; San Francisco; and Washington. By some estimates, they have been doing so since 1958. President Reagan knows this well. He sat on the Rockefeller commission and signed its final report concluding that such covert activities exist.
If we had any doubts about this eavesdropping effort, Arkady Schevchenko dispelled them when he came over in 1975 and subsequently defected in 1978. As you will recall, Schevehenko was, at the time, the second-ranking Soviet at the United Nations and an up-and-comer in the Soviet hierarchy. He describes the listening operation in New York City in his book Breaking With Moscow: "The rooftops at Glen Cove, the apartment building in Riverdale, and the Mission all bristled with antennas for listening to American conversations."
But we have to worry about more than just parabolic dish antennas tucked behind the curtains in the Soviet "apartment" building in Riverdale, New York.
There are also those Russian trawlers that travel up and down our coast. They are fishing, but fishing for what? Communications. And now the Soviets have taken their eavesdropping a step further and have built two new classes of AGI, or Auxiliary Gathering Intelligence, vessels. From the hull up, these new vessels are floating antennas, I suppose.
Most dangerous of all, perhaps, is the Soviet listening complex in Lourdes, Cuba, just outside Havana. This facility is the largest such Soviet listening facility outside its national territory. According to the president, it "has grown by more than 60 percent in size and capability during the past decade."
Lourdes allows instant communication with Moscow, and is manned by 2100 Soviet technicians. 2100!
By comparison, our Department of State numbers some 4400 Foreign Service Officers-total.
Again, to cite the recent Senate Intelligence Committee report: "The massive Soviet surveillance efforts from Cuba and elsewhere demonstrate . . . that the Soviet intelligence payoff from interception of unsecured communications is immense." Intelligence specialists are not prone to exaggeration, they do not last long that way. You can be assured that "massive" and "immense" are not subtle words as used in this context.
There are, however, two things you should know.
First, our most secret government messages are now protected from interception or are scrambled, and all classified message and data communications are secure. In addition, protected communications zones are being established in Washington, San Francisco and New York by rerouting most government circuits and by encrypting microwave links which continue to be vulnerable to intercept. But there are still communications links which carry unclassified, but sensitive, information that we need to protect.
Second, it is a truism in the intelligence field that while bits of information may be unclassified, in aggregate they can present a classified whole. The Senate Intelligence Committee informs us, "Due to inherent human weakness, government and contractor officials, at all levels, inevitably fail to follow strict security rules. . . .Security briefings and penalties were simply not adequate to prevent discussion of classified information on open lines." If the Soviets can piece it together, you must assume that they will, given the resources they invest toward this effort.
But the intelligence community needs no reminder that we are up against a determined and crafty opponent. In 1983, for example, a delegation of Soviet scientists were invited to tour a Grumman plant on Long Island. No cameras. No notes. All secure, right? Wrong. The delegation had attached adhesive tape to the soles of their shoes to gather metal fragments from the plant floor for further study at home. The Soviets are pretty good at metallurgy-probably the best in the world-and we don't need to help them any further.
But concern is not always translated into budgetary action, at least not in the realm of communications security. Let us take a look at the technical problem confronting us.
As you know, there are two basic ways voice can be transmitted over telephonic media: digital and analog. Analog refers to voice waves which are modulated (amplified) up to a very high frequency (HF). That is, they are increased in speed from hundreds of cycles per second to thousands of cycles per second. This facilitates their passage over distance.
Nevertheless, because analog radio waves diminish rapidly over distance, it's necessary to periodically amplify, or boost, the signal either at a microwave relay tower repeater or satellite transponder. (Actually, the signals are diminished in frequency to voice quality and then brought back up to high frequency.)
Digital transmissions are voice or data vibration signals which are converted into a series of on-and-off pulses, zeros and ones, as in a computer. Like analog telephone calls, digital calls go through a process of modulations and demodulation.
For the purposes of this discussion, we need only remember two things about analog and digital telephony.
First, analog telephony is fast being replaced by digital telephony because it better translates computer language. But, more importantly, after a high initial overhaul cost, it's possible to send thousands of digital calls (bundles) over a single conduit. Therefore, as we expand our digital capacity, we must ensure that both our analog and digital communications are protected from Soviet eavesdropping.
Second, sending bundles over a single conduit is the base block at which we introduce the encryption I am talking about.
When you place a long-distance telephone call from point A to point B, there are three communications paths, or circuits, over which your call might travel: microwave, satellite or cable.
Cable is the most secure. However, it is the least practical and economical method for bulk transmission over long distances. As a result, 90 percent of our long-distance telephone traffic is sent by microwave or satellite, and that which is in the air can be readily intercepted.
As your signal travels along the cable from your home to the local switching station and then on to a long-haul switching station, it is combined (stacked and bundled might better describe the process) with as many as 1200 other signals trying to get to the same region of the country.
This system of stacking and bundling signals is called multiplexing and it's how the telecommunications industry gets around the problem of 7 million New Yorkers all trying to call their senator at the same time on the same copper wire or radio frequency.
If you use a common carrier, that is, if you have not rented a dedicated channel from a telecommunications company, a computer at the long-haul switching station will select the first available route to establish a circuit over which your call signals may travel.
Therefore, calls that the caller believes to be on less vulnerable circuits may be automatically switched to more vulnerable ones. All this takes place in 1 to 3 seconds.
So let's follow your call as it goes by either microwave or satellite.
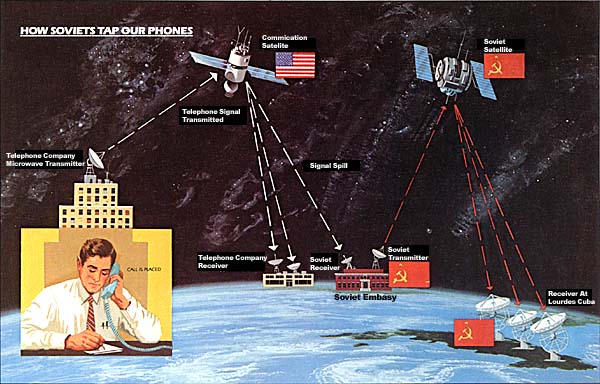
If your call goes via microwave, it will be relayed across the country as a radio wave in about 25-mile intervals from tower to tower (watch for the towers the next time you drive on an interstate route) until it eventually reaches a distant switching station where it is unlinked from the other signals, passed over cable to your friend's telephone, and converted back into voice.
The problem with this system: Along these microwave paths there is what we call "spill." This measures about 12.5 meters in width and the full 25 miles between towers. This is where the microwave signal is most at risk. Using a well-aimed parabolic dish antenna (located, let's say, on the top of Mount Alto, one of the highest hills in the District of Columbia, and site of the new Soviet embassy) you can intercept this signal and pull it in. And that is just what the Soviets are doing.
My solution: Throw the bastards out if they are listening to our microwave signals. Nothing technical about it. On three occasions I have introduced legislation requiring the president to do just that, unless in doing so, he might compromise an intelligence source. On June 7, 1985, this measure was adopted by the Senate as Title VII to the Foreign Relations Authorization Bill, but it was dropped in conference with the House of Representatives at the urging of the administration.
Nevertheless, I think the administration accepted the simple logic behind the proposal when at the end of October, 55 Soviet diplomats were ordered to leave the country, including, The New York Times tells us, "operatives for intercepting communications." Now, let's not let the Soviets just replace one agent with another.
The process is much the same for a satellite telephone call. Today, approximately eight telecommunications carriers offer satellite service using something like 25 satellites. Let's suppose your signal has traveled to a long-haul switching station and all microwave paths are filled. The carrier's computer searches for an alternative path to send the signal and picks out a satellite connection. At the ground station, your call is sent by a transponder up to a satellite and then down again to a distant ground station.
Using an array of satellite dishes at Lourdes, the Soviets can seize these signals from the sky just as a backyard satellite dish can pull in television (and telephone) signals. High-speed computers then sort through the calls and identify topics and numbers of particular interest. And if the information provided is real time intelligence, the Soviets have the ability to transmit it instantaneously to Moscow. And yes, the Soviets have the range at Lourdes to grasp our satellite transmissions as they travel from New York to Los Angeles or Washington to Omaha.
Here, too, there is a solution: Develop and procure cryptographic hardware for use at the common-carrier long-haul switching stations. This hardware will encrypt the multiplexed telephonic signals (that is, approximately 1200 calls at a time) before they are transmitted as radio waves from ground station to ground station, a technique analogous to the cable networks scrambling their signals. This can be done for under $1 billion. If we start by encrypting just those unclassified signals we categorize as sensitive, those having greatest impact on the national defense or foreign relations of the U.S. government, it would cost us about half as much. It would cost us so much more not to do so.
Communications security has no constituency. There is no tangible product and the public can never really be sure that we have done anything. But National Security Decision Directive 145 says it is a national policy and national responsibility to offer assistance to the private sector in protecting communications. It's time to make communications security (ComSec in the lingo) a true national security priority supported with resources as well as rhetoric. This was certainly the conclusion of the comprehensive Intelligence Committee report.
I agree, and have suggested a way to get on with it. If someone has a better idea-if you have another idea-I would be happy to know it. The important thing is that we stop this massive leak of sensitive information and protect your privacy.



