
Don't Let Them Bug You!
by Byron G. Wels
(Radio Electronics February 1969)
Despite new laws against electronic surveillance, "bugging" is a booming business.
Chances are somebody would like to listen in on your private conversations. And if they really want to, they can. However, there are steps you can take to foil the eavesdropper.
You'd be amazed who'd like to list in. Business competitors would like to know more about your business affairs so they can conduct theirs accordingly. People in your own firm would like to learn more about you-possibly to learn how best to impress you. Or your peers might like to short-circuit your attempts at promotion.
In your own home? Well, I don't want to sow seeds of doubt, but do you have a suspicious wife? How about your neighbors? Then, too, could business relations be anxious to overhear what you have to say in the privacy of your home?
If there's one common thread among people who have found that they're bugged, it's their surprise at the extent and detail to which a "spy" will go to accomplish his end.
 How bugs are planted
How bugs are planted
The easiest way to plant bugs is to have open access to the room. But this isn't really necessary. One recent case revealed that an office was being neatly tapped by a worker in the neighboring office who had rigged up a stethoscopic earphone to a small transistor amplifier. The pickup was a contact microphone of the type used on musical instruments, held firmly in contact with the separating wall between the offices-a wall that acted like a sounding board.
By far the most exotic applications are listening devices attached to telephones. You can purchase such units if you've got the price--$150 to $500. But they are easy enough to construct if you understand a bit about FM and telephones!
One such unit fits inside the telephone base. Once installed, the "spy" merely dials that number, and blows a small whistle into the mouthpiece of his phone. This signal keeps your phone from ringing, but from then until he hangs up his phone, the transmitter of your own phone will pick up room conversations and relay them to his telephone earpiece. Nice?
 Another device is about the size of a silver dollar. It's a printed-circuit unit, using integrated circuits. To install it, simply remove the mouthpiece cover from any telephone (it easily unscrews), then drop the phone company's transmitter button into your hand. Place the wafer-bug in the phone, drop the transmitter back and screw the cover down.
Another device is about the size of a silver dollar. It's a printed-circuit unit, using integrated circuits. To install it, simply remove the mouthpiece cover from any telephone (it easily unscrews), then drop the phone company's transmitter button into your hand. Place the wafer-bug in the phone, drop the transmitter back and screw the cover down.
This unit has an added feature. It draws its necessary 10 volts operating power from the telephone system each time you pick up the phone. The unit is a miniature FM transmitter, uses the telephone cords as an antenna and has a range of about 1000 feet, broadcasting to any nearby FM receiver tuned to the same frequency.
All bugs are not electronic. Another investigation recently revealed that a puzzling vital information leak was none other than an underpaid cleaning lady who came in at night to empty waste baskets and clean desks. Her careful cullings went to the competition, with a big fat bonus for her trouble.
Some electronic bugs are pretty elaborate in their simplicity. A 1" diameter blind hole can be quickly drilled on the underside of a wooden desk or table top. The mike button is placed in the hole and walnut wood filler is added to keep it in place. The wire leads are bonded to the wood with a dab of silver or copper conducting paint, which is then drawn along the underside, down a leg of the table, to a small hole in the carpeting. The silver conductive stripes are then covered with stain, and are totally invisible. Once under the carpeting, small wires can bring the signal to an amplifier and the "spy's" ears.
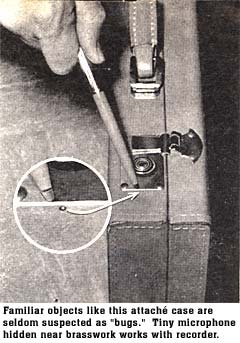 Lamps are another favorite location for eavesdroppers. The light bulb is removed and replaced with a soft plastic bulb which conceals a microphone. The lamp's line cord serves as conductor for the signal. The plastic light bulb? A mere 50 cents at any magic shop.
Lamps are another favorite location for eavesdroppers. The light bulb is removed and replaced with a soft plastic bulb which conceals a microphone. The lamp's line cord serves as conductor for the signal. The plastic light bulb? A mere 50 cents at any magic shop.
Bugging devices can be concealed just about any place in any room. Small FM transmitters designed for local broadcasting to a nearby tuner or receiver are easily hidden in a pack of cigarettes. Like a pack of cigarettes, they can be casually dropped behind a chair or hidden in a hollowed-out book.
How "safe" can you get?
For greatest protection against electronic eavesdroppers some organizations have resorted to building a room within a room. It's actually a small metal, wood and plastic box large enough to hold several people seated around a table. This windowless room sits on legs above the regular floor of the larger room and its roof falls somewhat short of the larger room's ceiling.
The walls of the secure room are designed so that they do not transmit sounds and they are electronically shielded. In addition, random noise generators operate in the larger outside room. The door to the secure room cannot be opened to admit a newcomer to a meeting until a red light first has flashed, and the occupants have stopped talking.
Why is such a drastic procedure necessary? Because even a newly built building can be "bugged." One of the simpler techniques of bugging a building under construction is to drop a protected microphone into wet concrete next to a steel reinforcing rod. The mike then cannot be located with a metal detector. Very thin wires are run from the mike, along steel girders and reinforcing rods and on water and sewer pipes to monitoring posts well away from the building.
 This was the sort of system uncovered in 1964 in the U.S. embassy in Moscow and in a brand new U.S. embassy in Warsaw, Poland. So remember, cost is the important factor. If your conversations are worth listening to, there may be extra ears listening.
This was the sort of system uncovered in 1964 in the U.S. embassy in Moscow and in a brand new U.S. embassy in Warsaw, Poland. So remember, cost is the important factor. If your conversations are worth listening to, there may be extra ears listening.
If you find one
If the "bugger" thinks you suspect him, chances are he'll plant a bug for you to find. He'll carelessly leave it in a vase of flowers or in a drawer. You find it, smash it and think you're safe. However, a smart surveillance man has several plants in any given room, so he can get good pickup wherever you move. If you find one, chances are there are others.
Look at it from the point of view of the guy planting the bugs. If he's a professional, he received a big fat fee for the job. The bugs themselves are expendable. He probably won't even attempt to recover the units, preferring to sacrifice them rather than run the additional risk of a second entry. If you find and smash a few of his units, he simply shrugs his shoulders and drives off.
 Nor does he care a hoot about what you call him. He's in a dirty business, so don't think you'll discourage him by stomping around the room and swearing.
Nor does he care a hoot about what you call him. He's in a dirty business, so don't think you'll discourage him by stomping around the room and swearing.
Once you find positive evidence that bugging is taking place, try to locate the devices themselves. Ask yourself where you would conceal them if you entered the room for the first time. If you find a unit, handle it with care and notify your company officers if the unit is found in your place of business, or the local police if it's in your home. Many commercial units have serial numbers that can lead authorities to the source, who might enable them to trace the buyer.
In one case inexpensive Citizens-band transceivers, locked in the transmit position, were found taped under an executive's desk. Their presence was not suspected, and they were revealed only when the tape let go and the unit dropped to the man's lap. Tracing the serial numbers and a bit of subsequent fingerprinting tied up the case.
Can you foil a bug?
 Sure you can-but it can be pretty expensive. There are firms that make a business of probing with electronic bug-detecting equipment. For a fee, they will electronically examine your home or office to check for the tell-tale signals that indicate a bug is operating.
Sure you can-but it can be pretty expensive. There are firms that make a business of probing with electronic bug-detecting equipment. For a fee, they will electronically examine your home or office to check for the tell-tale signals that indicate a bug is operating.
There are easier ways. Remember that a bug cannot always be placed for optimum sound pickup. The listening agent must compromise and settle for what he can get. It isn't hi-fi by a long shot. Placing bugs where they can't be seen doesn't mean the best sound pickup at all times.
The best and least expensive way to foil the listener is to lay a small transistor radio in the room where you're conversing. Pick a music station. The music blankets the full audio range, and any spoken words that the listener hears will be totally garbled by the music.
Another good foil is to arrange important conferences out of the office. A local luncheonette or bar, for example, usually provides a safe place to talk. But don't make appointments for such meetings over the telephone!
Modern industrial firms faced with similar problems have worked up new solutions. One major company hit on a novel answer. It created a conference room totally void of furniture and with a plain white tile floor, solid walls and ceilings. Only one door provides access to the room. The room is carefully examined before a conference, and the bare minimum of furniture is moved into the room just prior to the conference. People attending are also checked before admission, as are their clothing and other possessions. It's an almost foolproof system, but if a "bugger" wanted to, he'd probably find a way!
Recorders can be located
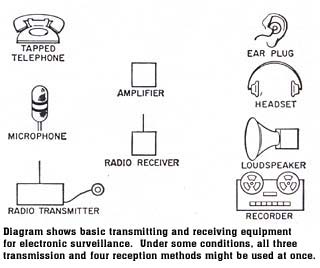
 The heart of any bugging system is the recorder that monitors and records the overheard conversation. Reliability is the paramount consideration. As a result, the eavesdropper may pay as much as $1,200 for a recorder.
The heart of any bugging system is the recorder that monitors and records the overheard conversation. Reliability is the paramount consideration. As a result, the eavesdropper may pay as much as $1,200 for a recorder.
Fortunately, it is possible to detect an operating recorder. As you know, when recording the magnetizing of the tape is not a simple linear function of the magnetic field acting on the tape. Actually, it is a non-linear process that can result in a distorted sound image. To overcome this, recorder manufacturers impose a high frequency bias of 20,000 to 100,000 Hz on the tape as it is recorded. This smoothes out many of the irregularities and improves the recorded effect.
This high-frequency signal is easily detected by a counterintelligence "sweeper" when he approaches the vicinity of the recorder. Placing the recorder in a shielded box will reduce and sometimes can eliminate the spurious signals making the recorder extremely difficult to locate.
When a recorder is used to tap a phone line, some detectable amount of the high-frequency signal may leak back onto the tapped phone line, even though the coil is not in physical contact with the line. As a result it is sometimes possible to detect a tapped line.
Using a specialist
Good counter-intrusion specialists do not come cheap. One top West Coast firm, Police Systems Inc., Santa Ana, Calif., is an excellent example of why. The company's vice president, Robert Jefferies arrives at clients' plants and offices in a late-model Lincoln fitted out from bumper to bumper, from floorboards to roof, with sophisticated electronic gear, most of it custom made. One receiver designed to pick up weak signals from a miniature transmitter several blocks away costs $55,000 and another one was delivered for $30,000.
The Lincoln is not an ostentation. Jefferies needs a large, roomy car heavy enough to bear the weight of his equipment and reliable enough to meet all sorts of unplanned situations.
Another Californian, Harold K. Lipset, an ace San Francisco investigator, has described a schedule of fees that is fairly typical of those charged by reputable agencies. To sweep the average office for bugs, Lipset service generally receives about $250. The fee for insuring the security of a small conference room runs about $100. A large classified meeting of 100 persons where each person, all chairs, table, fixtures and walls, floor and ceiling must be guaranteed secure, can lead to a bill upwards of $1,000.
Can I be sure?
Let's face facts. If somebody is bugging you, chances are that, unless professionals are involved, he will be using commonly available devices. Certainly the telephone is worthy of careful examination and scrutiny. If you're really worried about the phone, you can get a scrambler and unscrambler, which electronically chops up your phone conversations so that the eavesdropper will be mystified by the garbled sounds he hears. The party to whom you are speaking must also be equipped with this device.
Bugs planted in a room, unless placed by a professional, are usually one of two types: wireless and wired. The latter need conductors to bring the information to the bugger, and the best way to locate them is to look for wires that don't belong in the room. Also examine ventilators and concealment areas-behind radiators or in lamp shades.
Wireless types are either FM or Citizens-band units. Both are easy to detect. Get a small FM receiver, and tune it across the band. Pay particular attention to frequencies between the regular broadcasting stations, and listen for a hiss. When you hear that, start talking. If you hear your own voice coming out of the FM receiver, you can bet that it's coming out of the bugger's receiver also!
To check for CB bugging, use a CB unit in the receive mode, and switch from channel to channel, whistling or speaking at each channel.
But don't worry for too long. In the course of preparing this article, we came across a case where a firm didn't plant bugs in the competition's office-instead they planted rumors that they HAD planted bugs! The result? Weeks of confusion while the competition ran around and spent a small fortune trying to locate nonexistent bugs!
|



